45 aws best practices
Best Practices for Running Oracle Database on AWS WebNov 18, 2021 · However, there are a number of AWS platform considerations relating to security, storage, compute configurations, management, and monitoring that will help you get the best out of your Oracle Database implementation on AWS. This whitepaper provides best practices for achieving optimal performance, availability, and reliability, … Best practices for working with AWS Lambda functions WebBest practices for using AWS Lambda. REPORT RequestId: 3604209a-e9a3-11e6-939a-754dd98c7be3 Duration: 12.34 ms Billed Duration: 100 ms Memory Size: 128 MB Max Memory Used: 18 MB
AWS account root user - AWS Identity and Access Management WebThis identity is called the AWS account root user and is accessed by signing in with the email address and password that you used to create the account. ... As a best practice, safeguard your root user credentials and don't use them for everyday tasks. Root user credentials are only used to perform a few account and service management tasks.
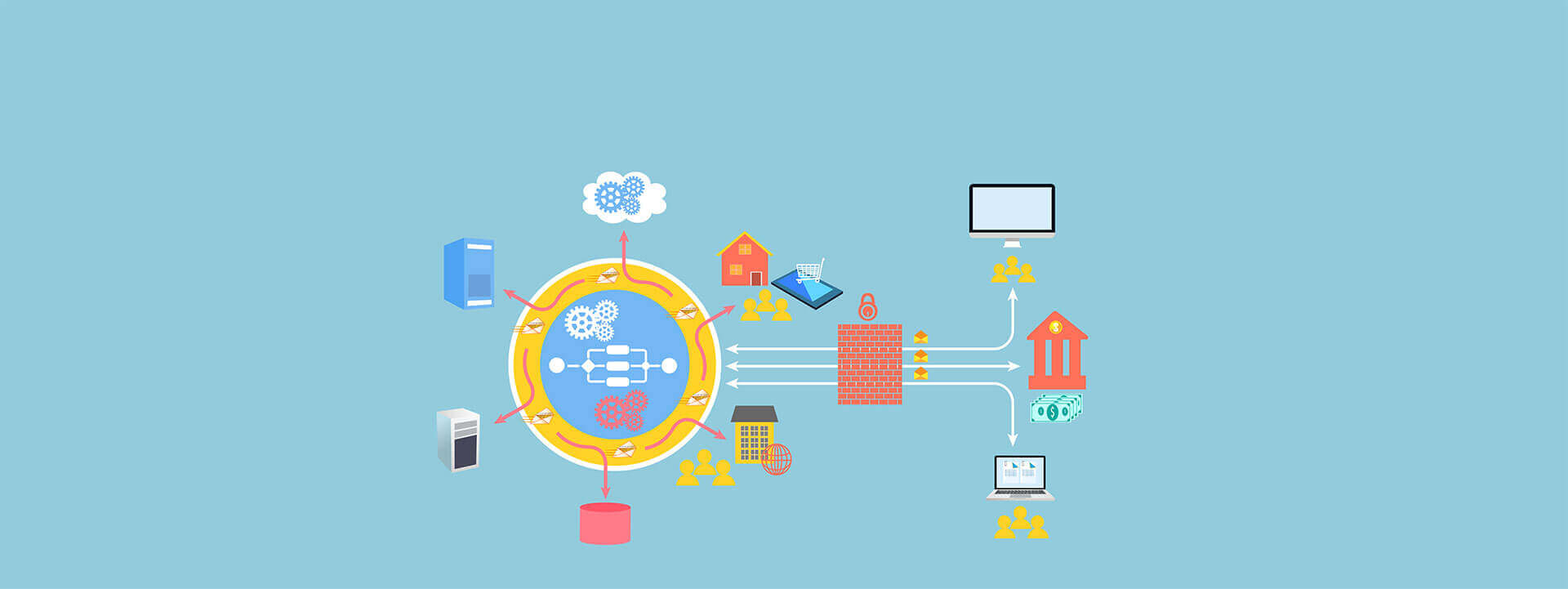
Aws best practices
Establishing your best practice AWS environment WebThe rest of this guide will walk you through the elements of building a secure and productive multi-account AWS environment, often referred to as a “landing zone,” as recommended by AWS. This represents the best practices that can be used to build an initial framework while still allowing for flexibility as your AWS workloads increase over ... Security best practices in IAM - AWS Identity and Access … WebJul 14, 2022 · Use the root user to complete the tasks that only the root user can perform. For the complete list of these tasks, see Tasks that require root user credentials in the AWS General Reference. For more information, see Best practices to protect your account's root user in the AWS Account Management User Guide. Introduction - EKS Best Practices Guides - GitHub Pages Best Practices for Cluster Autoscaling: karpenter, cluster-autoscaler; Best Practices for Running Windows Containers; Best Practices for Networking; We also open sourced a Python based CLI (Command Line Interface) called hardeneks to check some of the recommendations from this guide. In the future we will be publishing best practices guidance ...
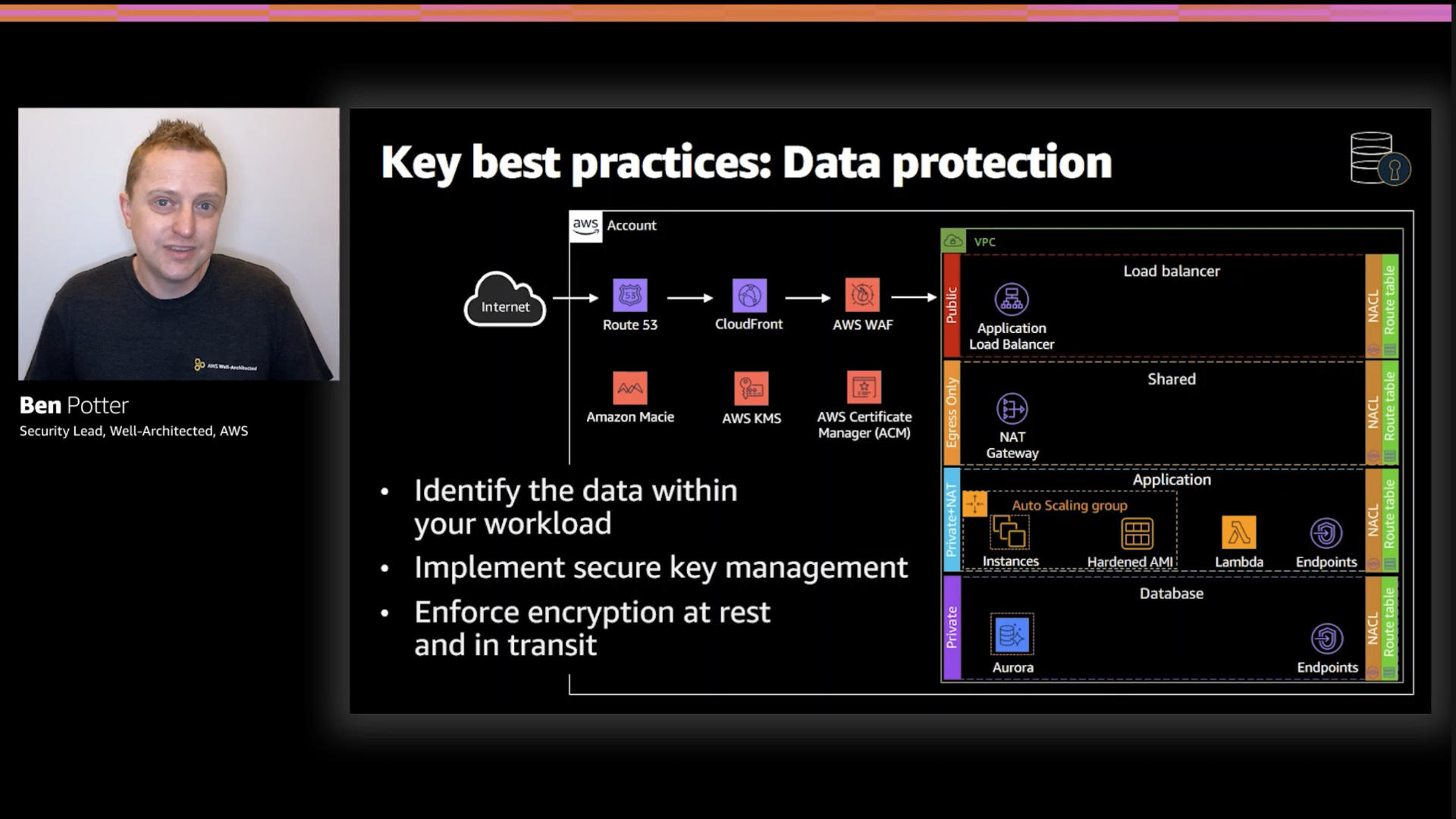
Aws best practices. Security best practices for Amazon S3 WebEnable AWS Config. Several of the best practices listed in this topic suggest creating AWS Config rules. AWS Config enables you to assess, audit, and evaluate the configurations of your AWS resources. AWS Config monitors resource configurations, allowing you to evaluate the recorded configurations against the desired secure configurations. Best practices for AWS accounts - AWS Account Management WebBest practices for AWS accounts. This section describes best practices that we recommend that you follow with your AWS accounts. They are arranged in the following categories: Topics. Best practices to protect your account's root user; Best practices for managing AWS access keys ... Best practices for Amazon EC2 - Amazon Elastic Compute Cloud WebBest practices for Amazon EC2. To ensure the maximum benefit from Amazon EC2, we recommend that you perform the following best practices. Security. Manage access to AWS resources and APIs using identity federation, IAM users, and IAM roles. Establish credential management policies and procedures for creating, distributing, rotating, and ... Best practices for AWS Organizations - AWS Organizations WebBest practices for AWS Organizations. We recommend that you follow these best practices when you create and operate your organization. Topics. Best practices for the management account; Best practices for member accounts Document Conventions. Tutorial: Monitor with CloudWatch Events. Best practices for the management account ...
Introduction - EKS Best Practices Guides - GitHub Pages Best Practices for Cluster Autoscaling: karpenter, cluster-autoscaler; Best Practices for Running Windows Containers; Best Practices for Networking; We also open sourced a Python based CLI (Command Line Interface) called hardeneks to check some of the recommendations from this guide. In the future we will be publishing best practices guidance ... Security best practices in IAM - AWS Identity and Access … WebJul 14, 2022 · Use the root user to complete the tasks that only the root user can perform. For the complete list of these tasks, see Tasks that require root user credentials in the AWS General Reference. For more information, see Best practices to protect your account's root user in the AWS Account Management User Guide. Establishing your best practice AWS environment WebThe rest of this guide will walk you through the elements of building a secure and productive multi-account AWS environment, often referred to as a “landing zone,” as recommended by AWS. This represents the best practices that can be used to build an initial framework while still allowing for flexibility as your AWS workloads increase over ...




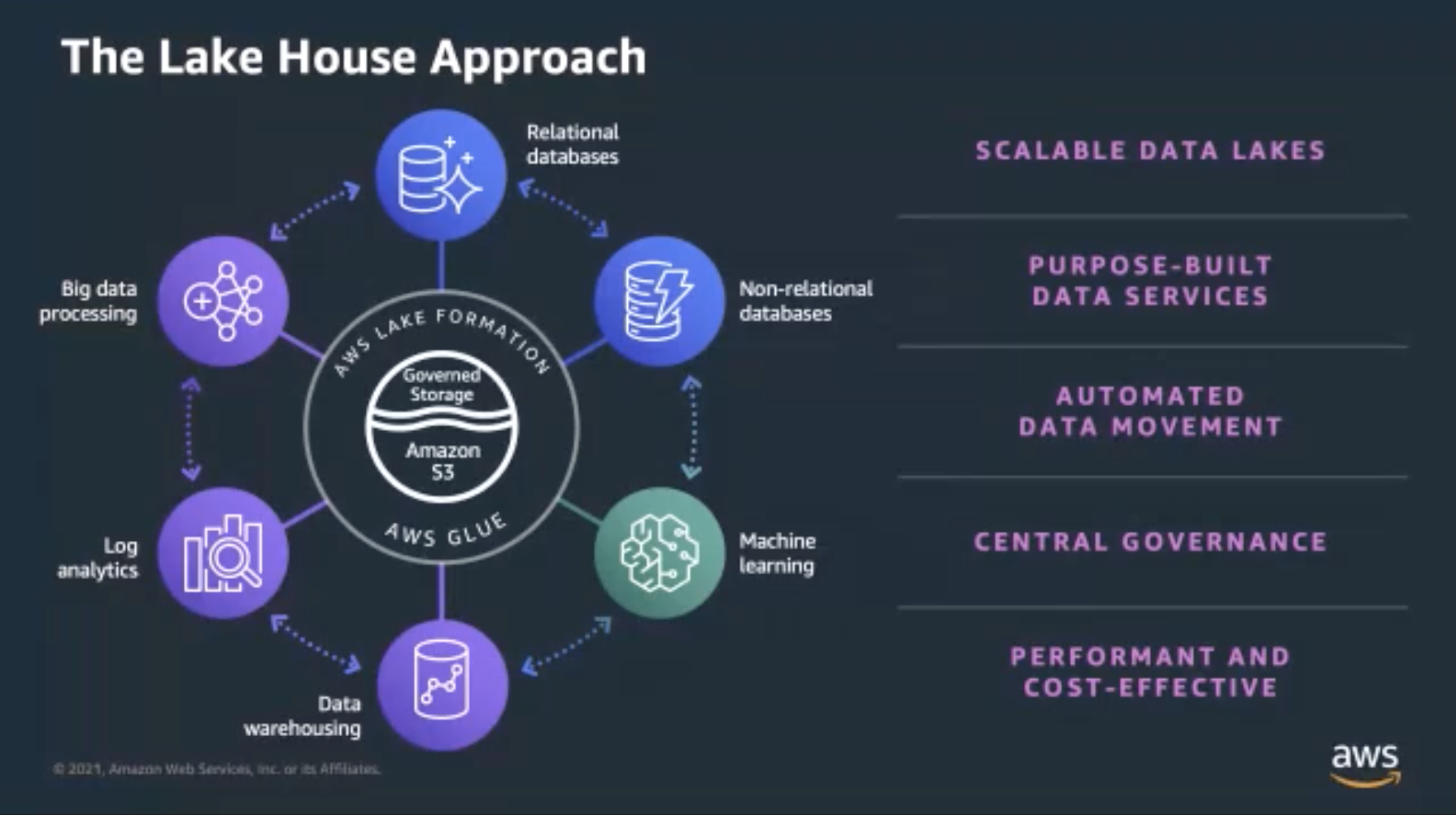

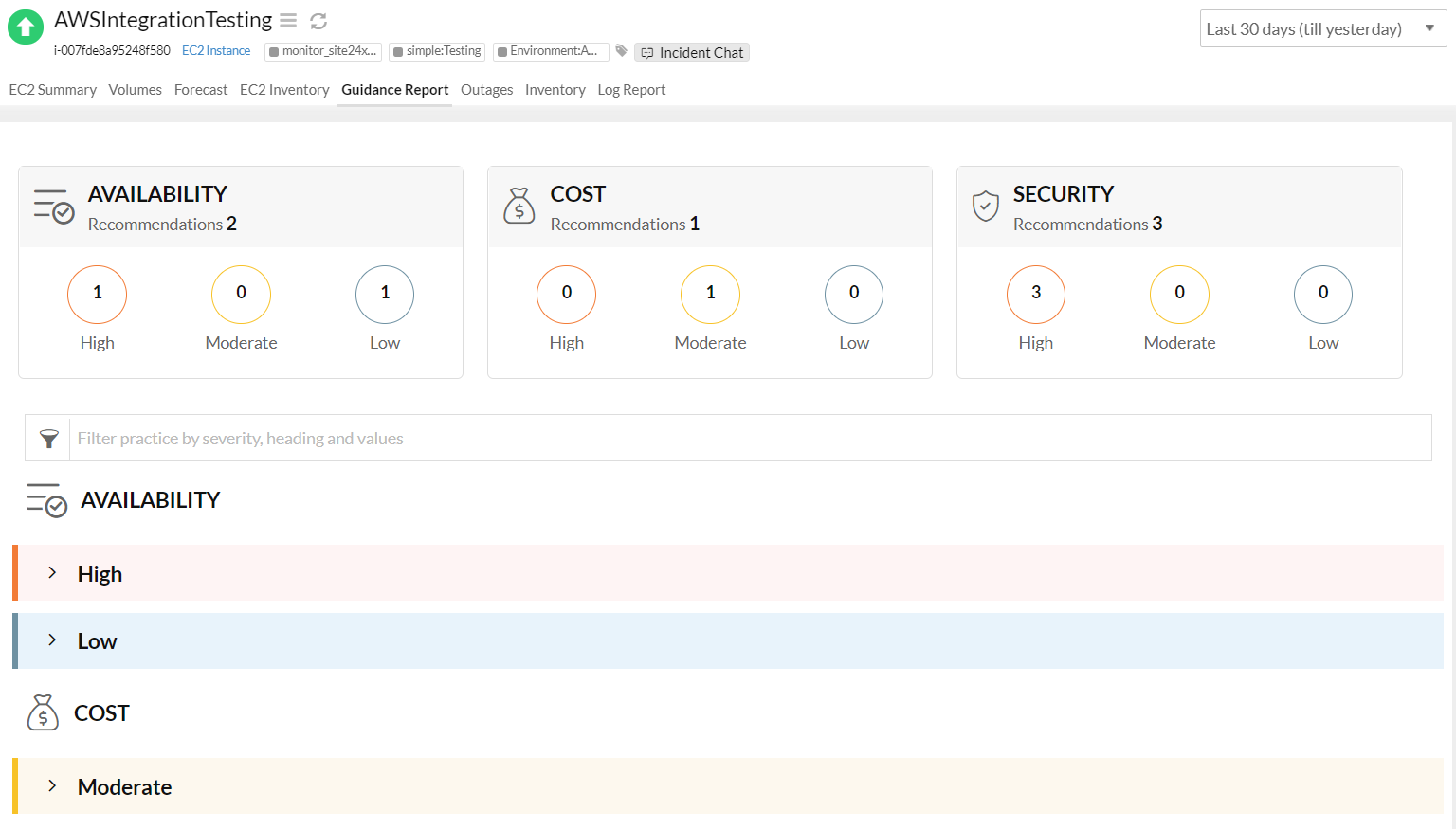
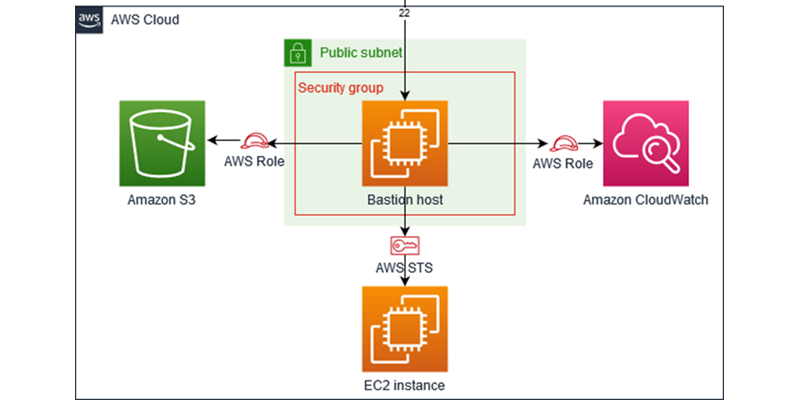
![AWS IAM: Best practices [Part 1] – DEVOPS DONE RIGHT](https://blog2opstree.files.wordpress.com/2021/03/image-36.png)





















0 Response to "45 aws best practices"
Post a Comment